Belkasoft Adds Forensic Support for Windows Phone 8.1
Belkasoft updates its digital forensic solution, Belkasoft Evidence Center 2015, with the ability to perform forensic analysis of Windows Phone 8.1 images acquired via JTAG flashers and Cellebrite UFED hardware.
The new release enables automated extraction, discovery and analysis of user data available in chip-off dumps acquired from mobile devices running Windows Phone 8 and 8.1. Supported data includes Web browsing histories, contacts, call logs, chats, instant message conversations, cached social network communications, screenshots of background applications, and many other types of data.
Analyzing Windows Phone 8.1 Dumps
The new release of Belkasoft Evidence Center 2015 enables full support for information dumped or extracted from all Windows Phone 8.1 devices with the use of JTAG or UFED hardware. Belkasoft Evidence Center 2015 can parse the binary dumps, reconstructing the original file system of the device and enabling experts browse, view and extract individual files and folders. The tool will automatically search for, extract and analyze the many types of evidence recognized by Belkasoft Evidence Center including contacts and address books, call logs, communication histories in Skype and third-party messenger apps, browsing history and cached social network conversations.
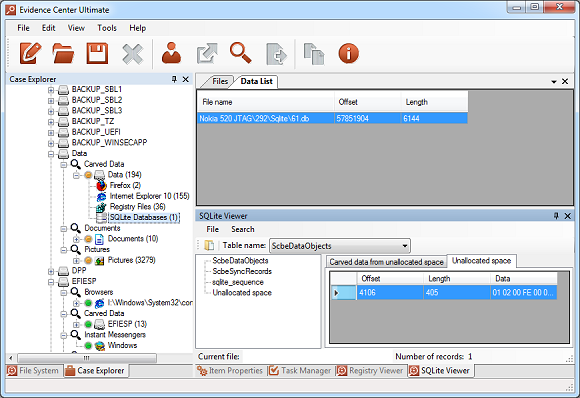
SQLite database, carved from JTAG dump, is shown in the built-in SQLite Viewer
Page File Analysis
Similar to its desktop counterpart, the mobile version of Windows swaps memory pages into a page file. Considering the domination of low-memory devices with only 512 MB of RAM, their reliance on page files is extremely strong. However, due to the different microprocessor architecture, the format and content of the page file differs significantly. At the same time, page files contain a host of forensically important information, preserving snapshots of the device’s volatile memory and containing essential real-time information that would be otherwise lost once device has been powered off.
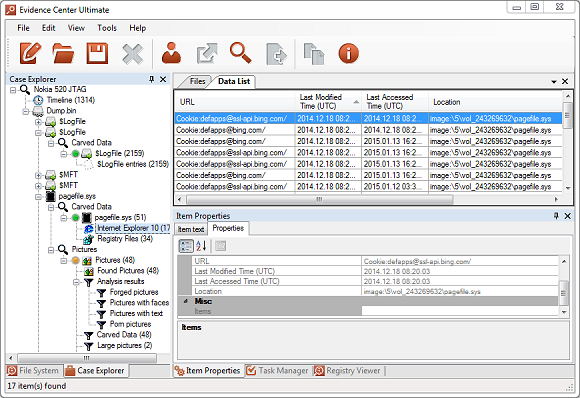
Internet Explorer history is found inside pagefile, located in JTAG dump
Belkasoft Evidence Center becomes the first digital forensic tool to parse Pagefile.sys files produced by Windows Phone 8.1. The tool will automatically parse the page file, carving all known types of artifacts such as cached Web pages and pictures, chat messages and posts in social networks.
Screenshots of Minimized Applications
Windows Phone devices can only run one app in the foreground. Background applications are minimized and often pushed out of the volatile memory. At the time Windows Phone minimized an app, the system captures and stores its screenshot. Depending on the application, the screenshot may display current user activity such as the currently visited Web page or social network profile, open chat session, picture or video being viewed. Information captured with these screenshots is often unavailable elsewhere. Belkasoft Evidence Center recognizes the importance of application screenshots, targeting these pictures specifically during carving and displaying them in a dedicated section.
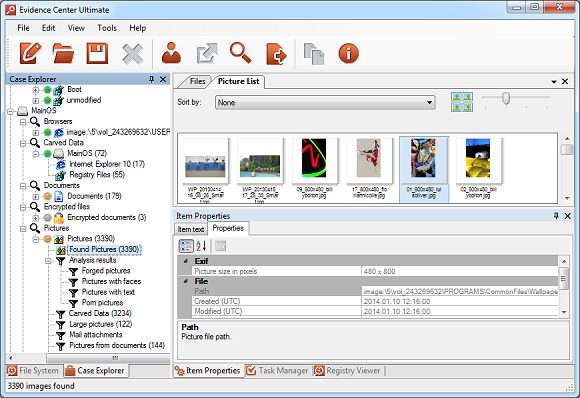
A pack of application screenshots found inside particular JTAG dump
About Belkasoft Evidence Center 2015
Belkasoft Evidence Center is a digital forensic solution enabling security experts and forensic specialists collect and analyze digital evidence from computer and mobile devices. Belkasoft Evidence Center can automatically locate, process and analyze evidence stored inside hard drives, forensic images and dumps. Hundreds of evidence types supported out of the box, such as documents, emails, pictures and videos, chats and browser histories, encrypted and system files.
Low-level access to hard disk and system structures means that even data that’s been deleted by a suspect cannot escape from investigators. Supporting Windows, Unix/Linux, Android and Mac OS X file systems, natively mounting images created in EnCase and FTK, DD and SMART formats, UFED, chip-off and JTAG binary dumps, X-Ways containers and many popular virtual machines without using these or any third-party tools, Belkasoft Evidence Center can collect more evidence than any single competing tool in its class.
Information on Belkasoft Evidence Center as well as the free demo download are available at
